ARE employees who lost their jobs during the pandemic a cybersecurity risk? Armed with passcodes and access information, former employees, especially those who were either retrenched or fired for cause, amidst the difficult times of the pandemic, could resort to revenge attacks, revealing company secrets or causing mayhem in a company’s email network or Cloud server.
Despite known security measures in place, and turnovers and resetting of passwords, and access codes enacted, only half (51 percent) of the heads of small and medium businesses (SMB) interviewed in a Kaspersky survey are confident that their ex-employees can’t access the company’s digital assets. This recent study, involving 1,300 business leaders in small and medium-sized organizations, shows that staff reductions “may cause additional cybersecurity risks.” Just 53 percent of those surveyed are sure that former workers can’t use corporate accounts.
“This problem becomes more complicated when employees actively use non-corporate or ‘shadow IT’ services which are not deployed or controlled by corporate IT departments. If the usage of these services is not managed after an employee is dismissed, there is little chance that access to information shared via these applications will be shut off for a former worker,” Alexey Vovk, Head of Information Security at Kaspersky explained.
Many companies during the pandemic looked for novel ways to reduce costs but cybersecurity was not one of them. Cutting down on the workforce was seen as a last result and companies focused on team retention rather than save budget.
Not all companies had that luxury. Many businesses axed employees in order to reduce costs during hard times. The behavior of SMBs employees fired during the lockdowns were considered in the study. Kaspersky also studied how businesses reacted and what tactics they chose to keep their business afloat, as well as what cybersecurity risks anti-crisis measures they applied.
Given that almost half of respondents couldn’t confidently claim that their ex-employees didn’t have access to their company’s digital assets, reductions in staffing may put the safety of data and company livelihood at additional risks.
Ex-employees misuse of data in new jobs or to drum up business for themselves were major concerns for bosses. The survey results suggest that most business leaders are worried that former employees will share the company’s internal data with new employers (63 percent) or use corporate data such as previous client databases, to launch their own business (60 percent).
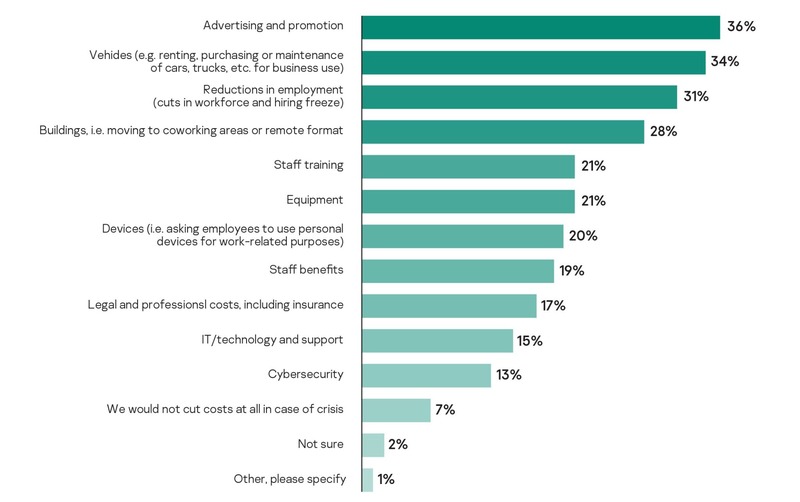
Overall, 31 percent of respondents consider reductions in employment as a possible measure to cut costs in case of a crisis. Other popular cost-cutting steps include a decrease in spending for advertising and promotion (36 percent) and vehicles (34 percent).
“Unauthorized access can become a huge problem for any business, affecting the competitiveness of a company when corporate data is transferred to a competitor, sold off, or deleted,” explains Alexey Vovk, Head of Information Security at Kaspersky.
Kaspersky also reported in a recent that phishing incidents continue to skyrocket in Southeast Asia (SEA). The latest data revealed that it only took six months for cybercriminals to exceed their phishing attacks last year against users from the region.
From January to June 2022, Kaspersky’s Anti-Phishing system blocked a total of 12,127,692 malicious links in SEA. It is 1 million more than the total number of phishing attacks detected here in 2021 — 11,260,643. More than half of these phishing detections were done to users in Malaysia, the Philippines, and Vietnam.
“The first half of 2022 is eventful in good and bad ways. On a personal level, we went through the seismic shift of trying to regain our lives post-pandemic, forcing companies and organizations to welcome remote and hybrid work. The travel sector, including airlines, airports, travel agencies, and more, has also been overwhelmed by the influx of tourists wanting to travel with borders now open,” Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky elaborated.
Yeo said that behind these shifts are networks and systems that needed to be updated and secured hastily. Cybercriminals are all ears and with their ability to tweak their messages and infuse them with believable urgency. “As a result, we’ve seen real, unfortunate incidents of victims losing money because of phishing attacks,” he adds.
To make sure that uncontrolled accesses and shadow IT won’t affect your company’s efficiency and security, Kaspersky recommends the following steps:
-
Keep control of the number of people with access to crucial corporate data, reducing the amount of data available to all employees. Breaches are more likely to occur in organizations where too many employees work with confidential valuable information that can be sold or somehow used.
-
Set up a policy for access to corporate assets, including email boxes, shared folders, and online documents. Keep it up to date and remove access if an employee leaves the company. Use cloud access security broker software that helps manage and monitor employee activity within cloud services and enforces security policies;
-
Make regular backups of essential data to ensure corporate information stays safe in case of emergency;
-
Provide clear guidelines on the usage of external services and resources. Employees should know which tools they should or shouldn’t use and why. When switching to any new software for work, there should be a clear procedure of approval with IT and other responsible roles;
-
Encourage employees to have strong passwords for all digital services they use and to change passwords regularly;
-
Regularly remind staff about the importance of following basic cybersecurity rules relating to safe account and password management, email security, and web browsing. A comprehensive training program will allow your workers not only gain the necessary knowledge but also to apply it in practice;
-
Employ dedicated cybersecurity services which provide visibility over cloud services, such as Kaspersky Endpoint Security Cloud.




